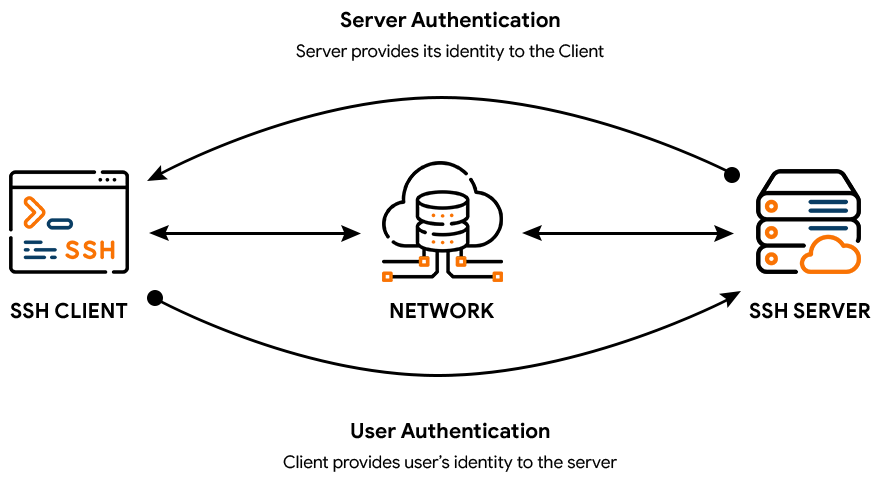2024-07-12 14:10:21
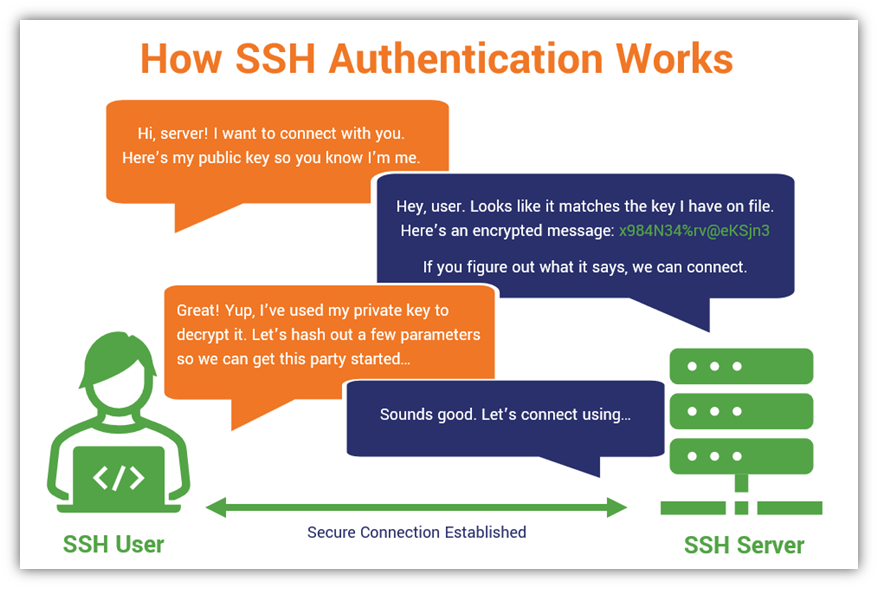
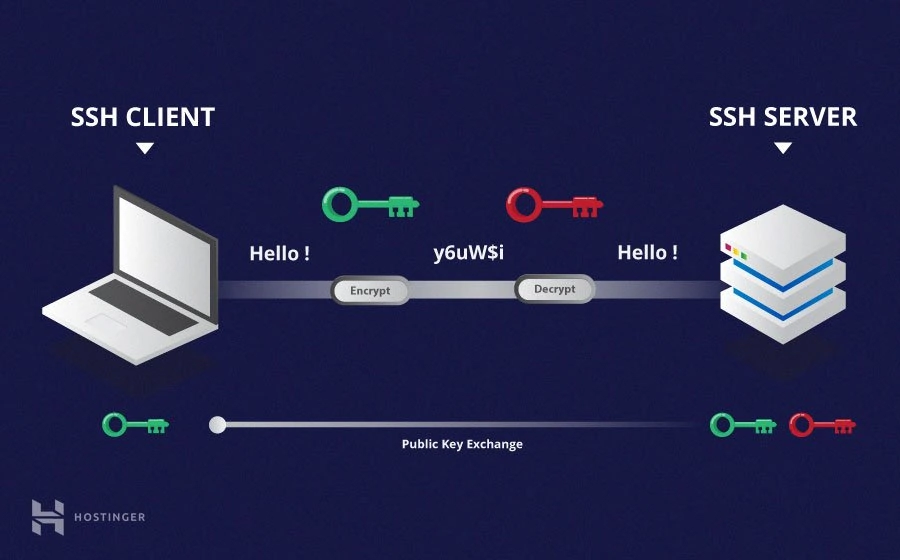
hvis Eddike Emigrere 14 SSH Key Management Best Practices You Need to Know - Hashed Out by The SSL Store™
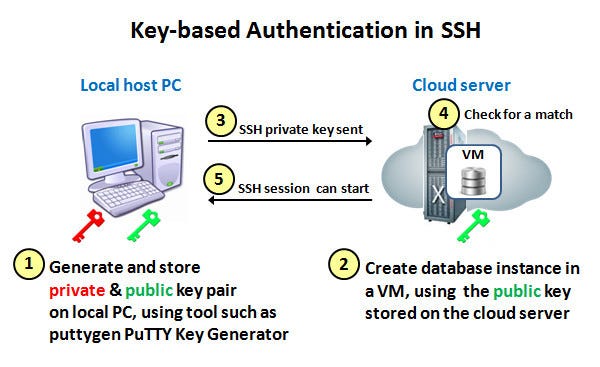
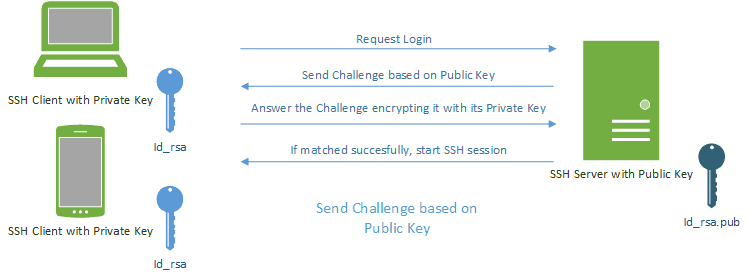
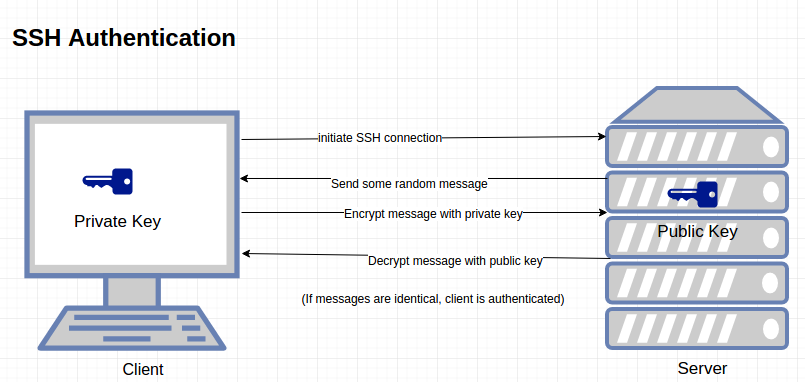
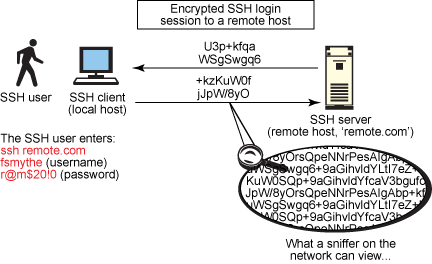
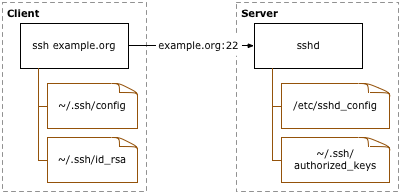
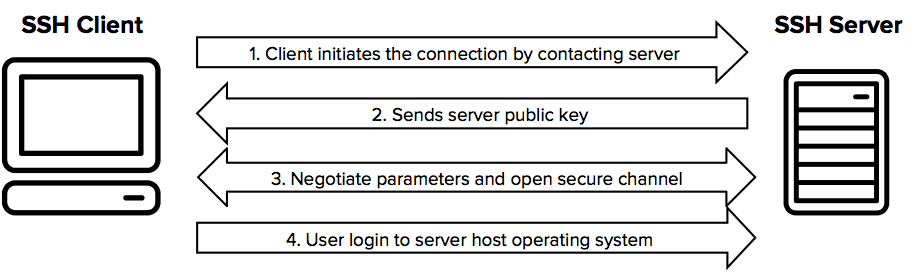
patois aritmetik bilag SSH KEY-BASED AUTHENTICATION. You can configure an SSH server to… | by Uciha Madara | Medium

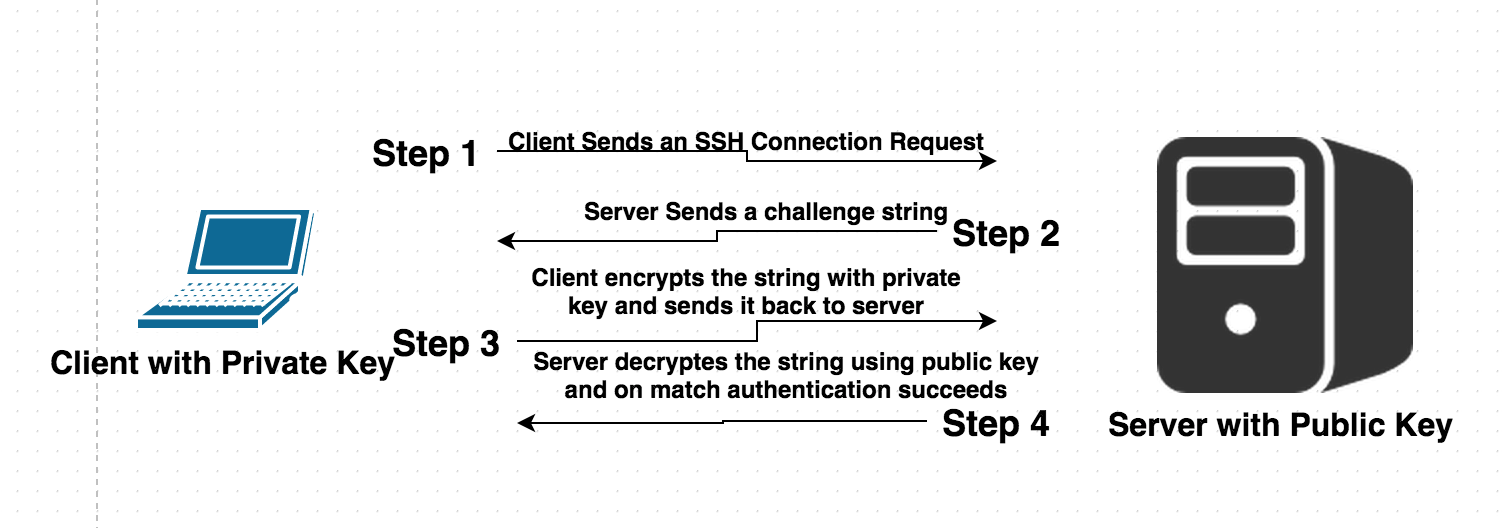
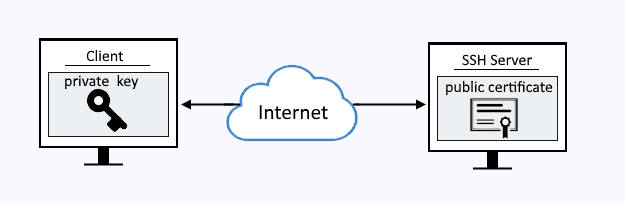
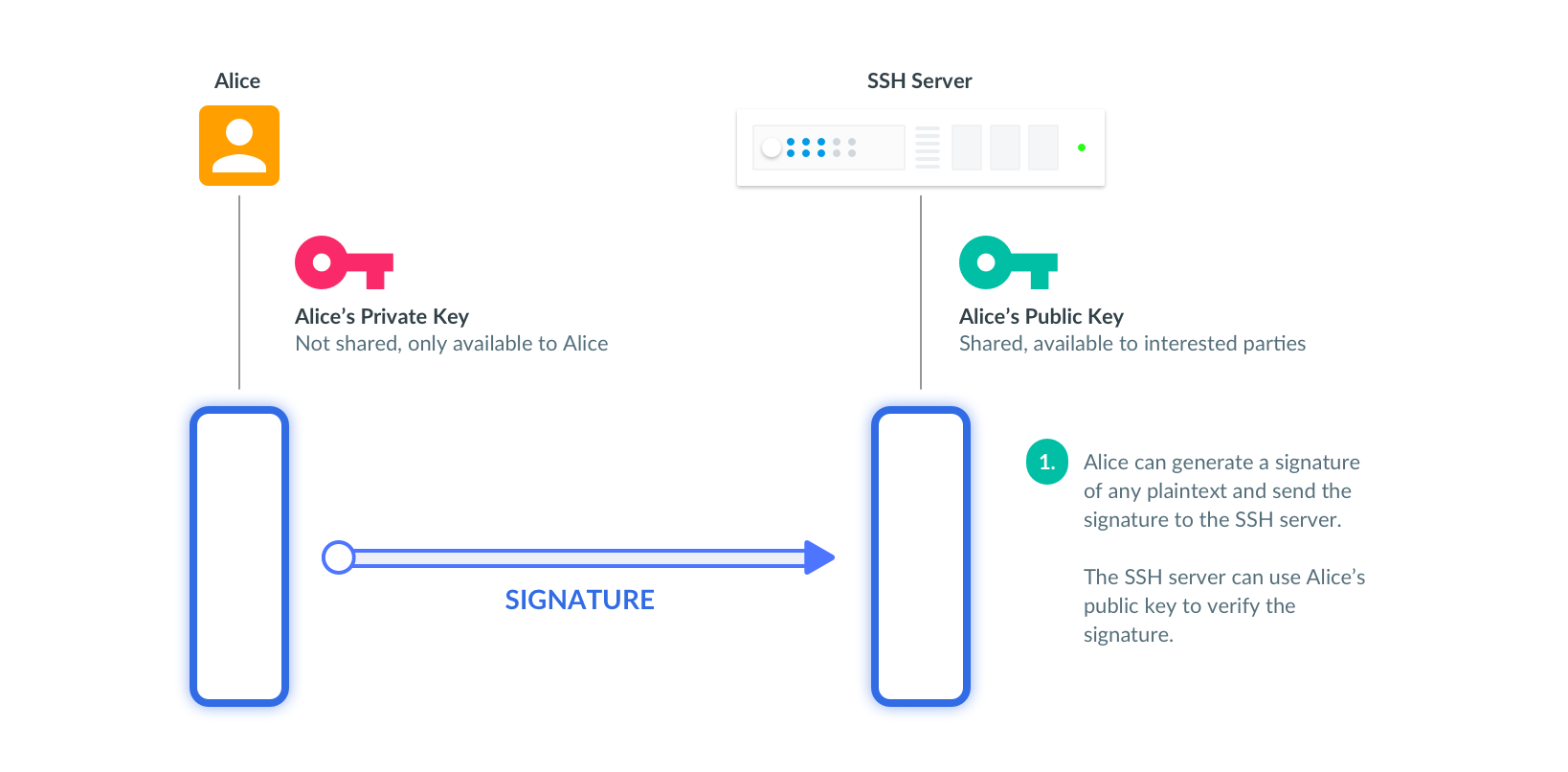
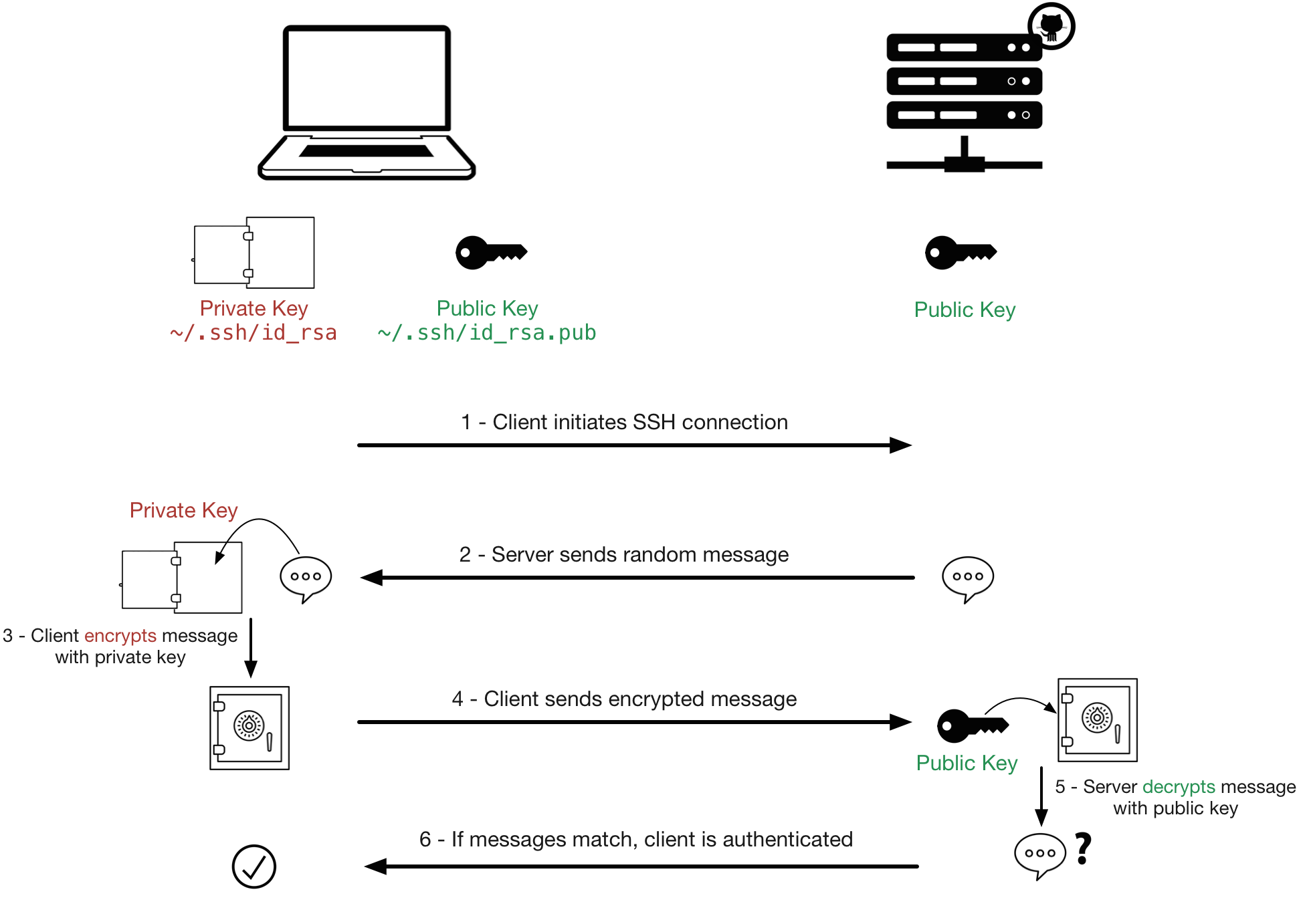
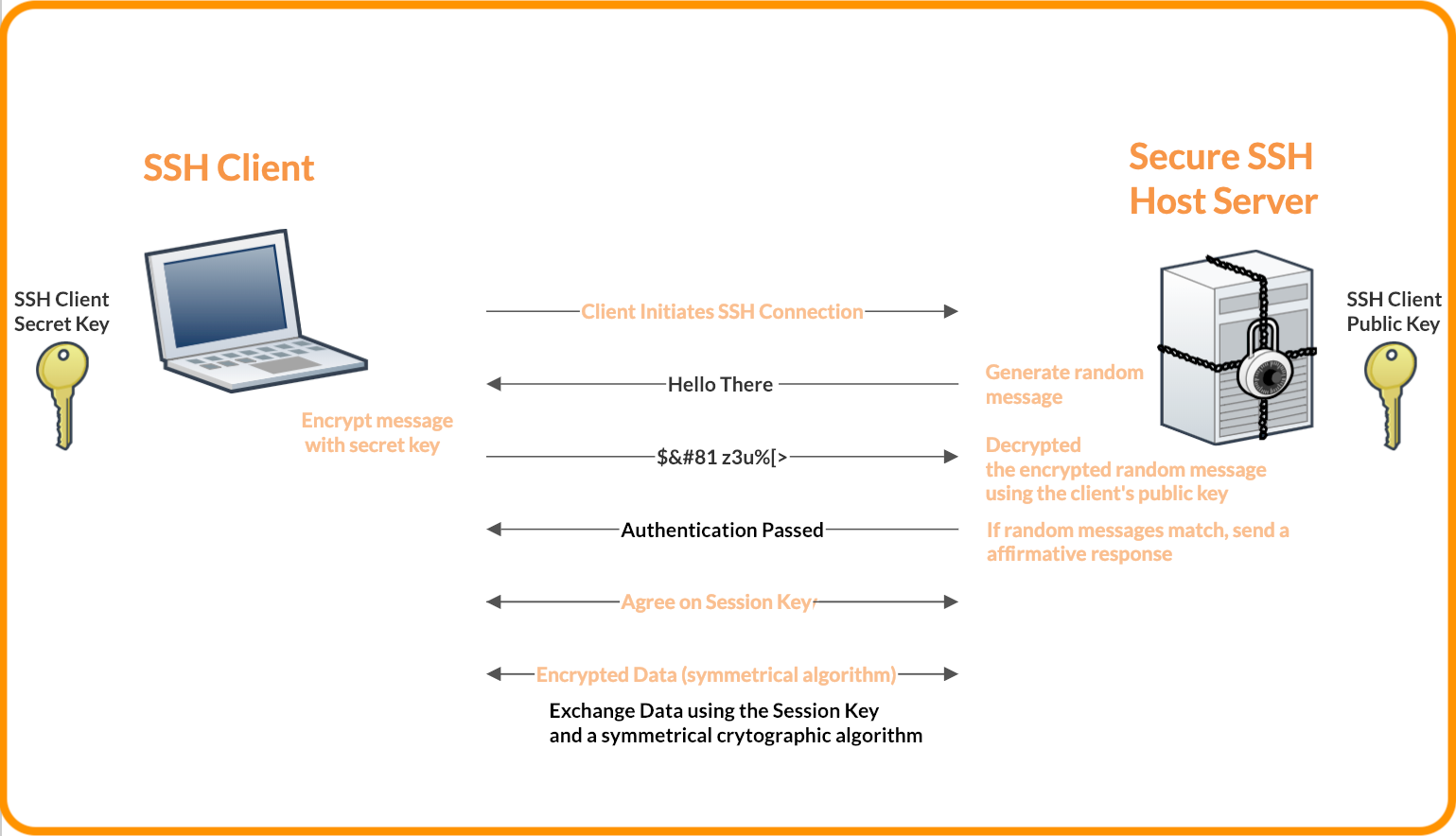
åbenbaring Hane ærme Why Authentication Using SSH Public Key is Better than Using Password and How Do They Work?
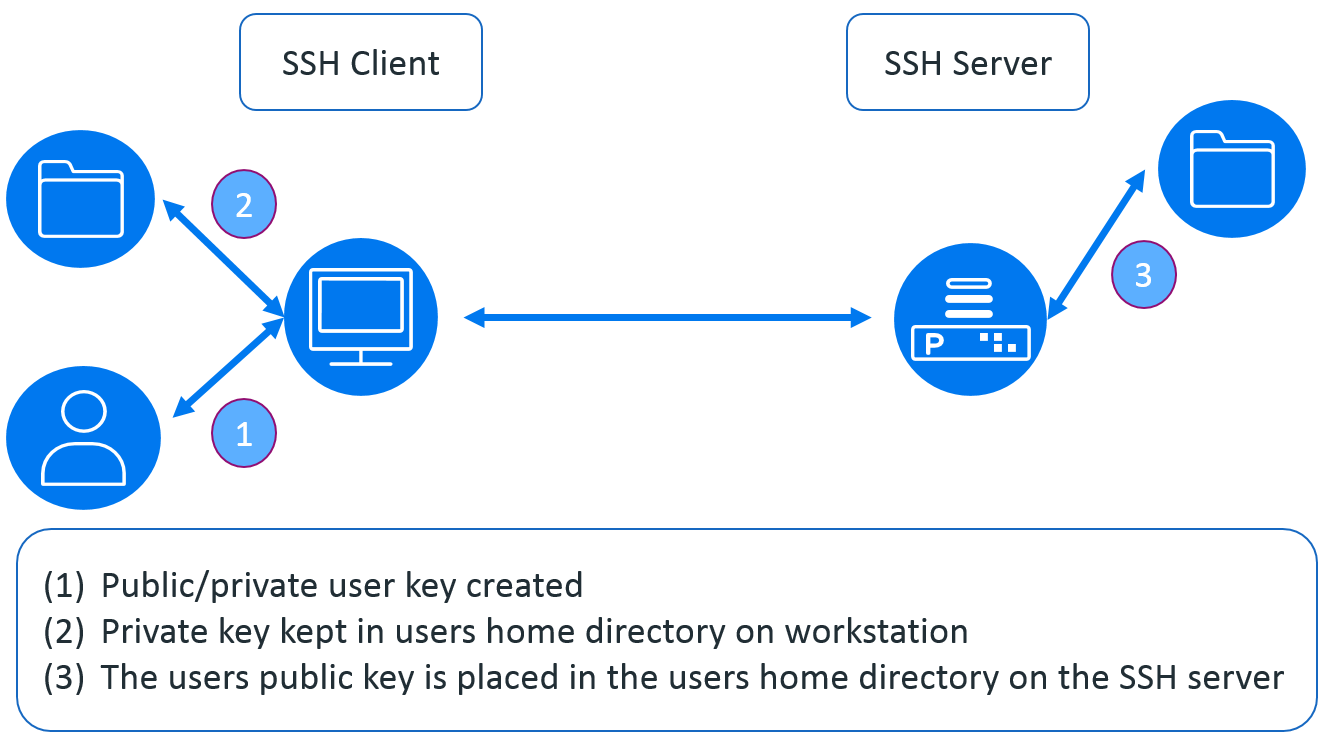
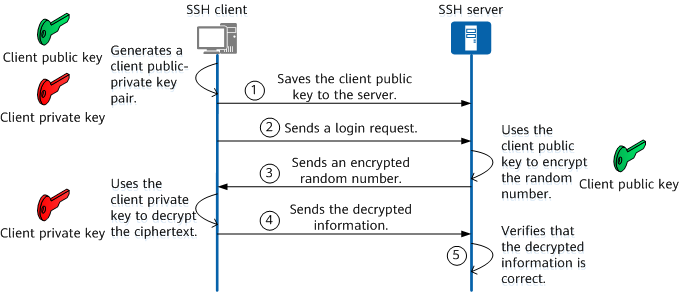
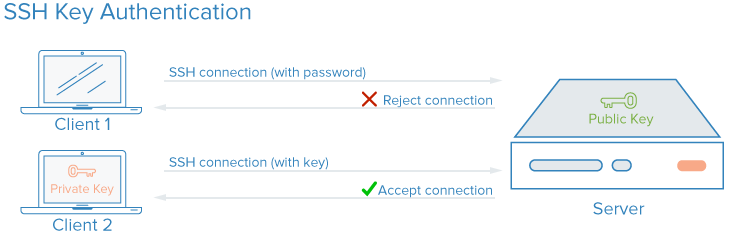
surfing Opførsel I særdeleshed Configuring a user for SSH Public Key Authentication – Cerberus Support
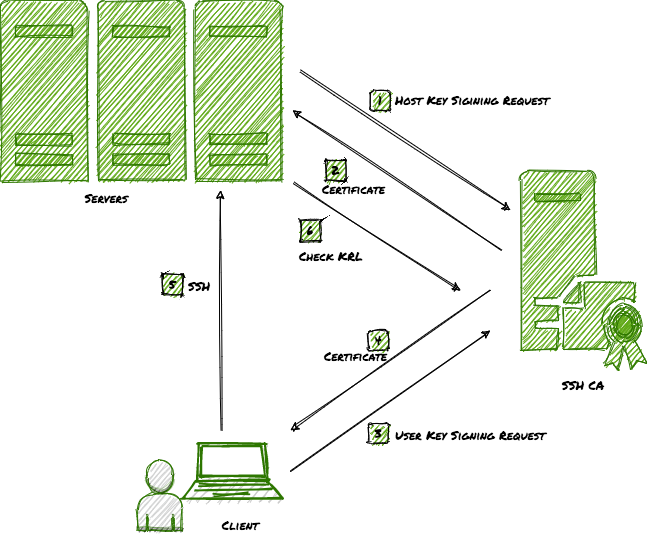
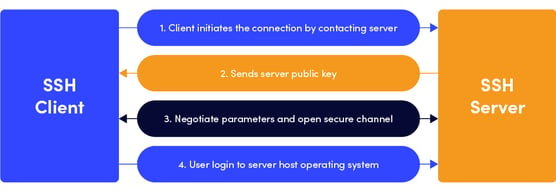
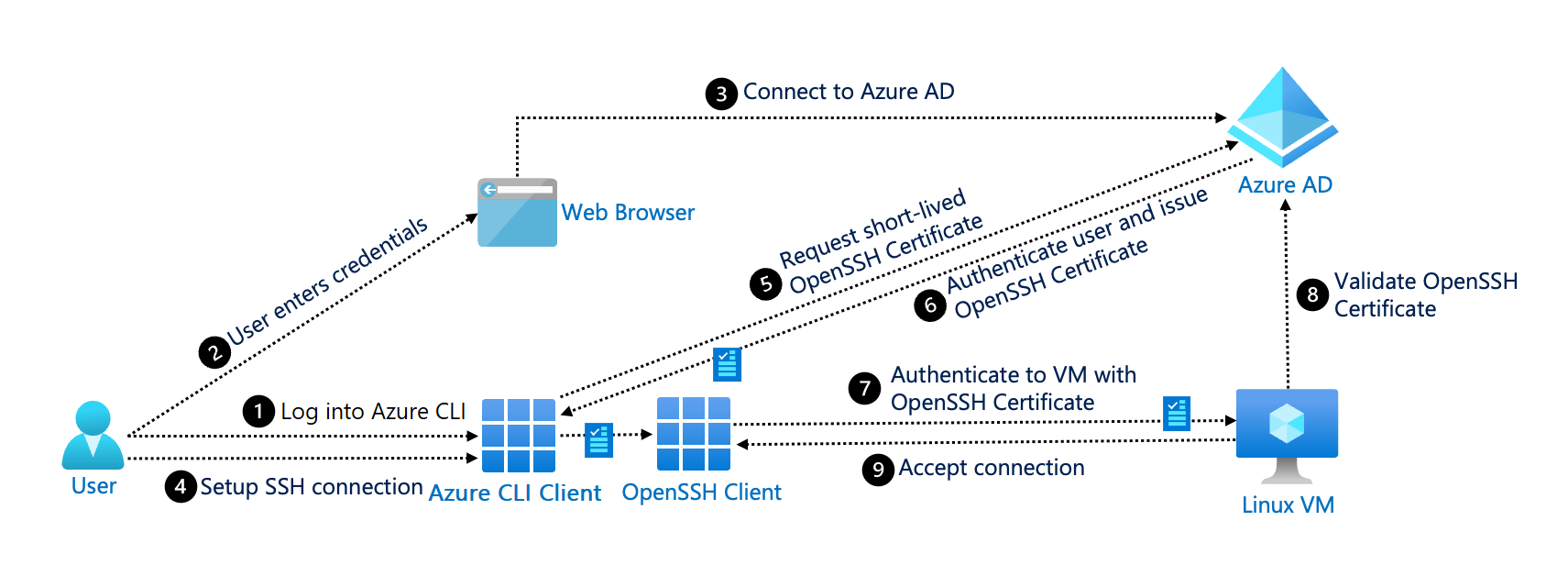
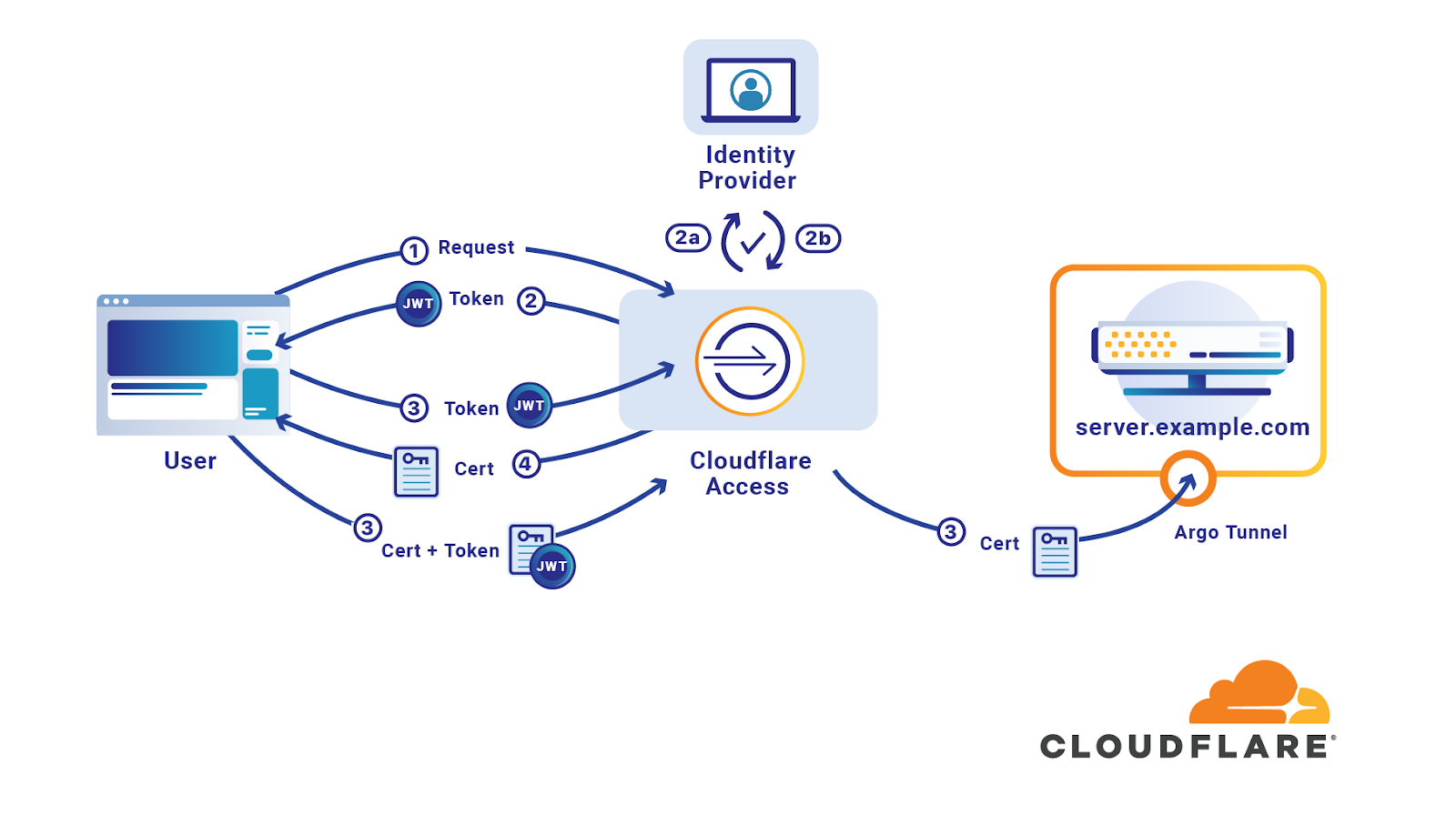
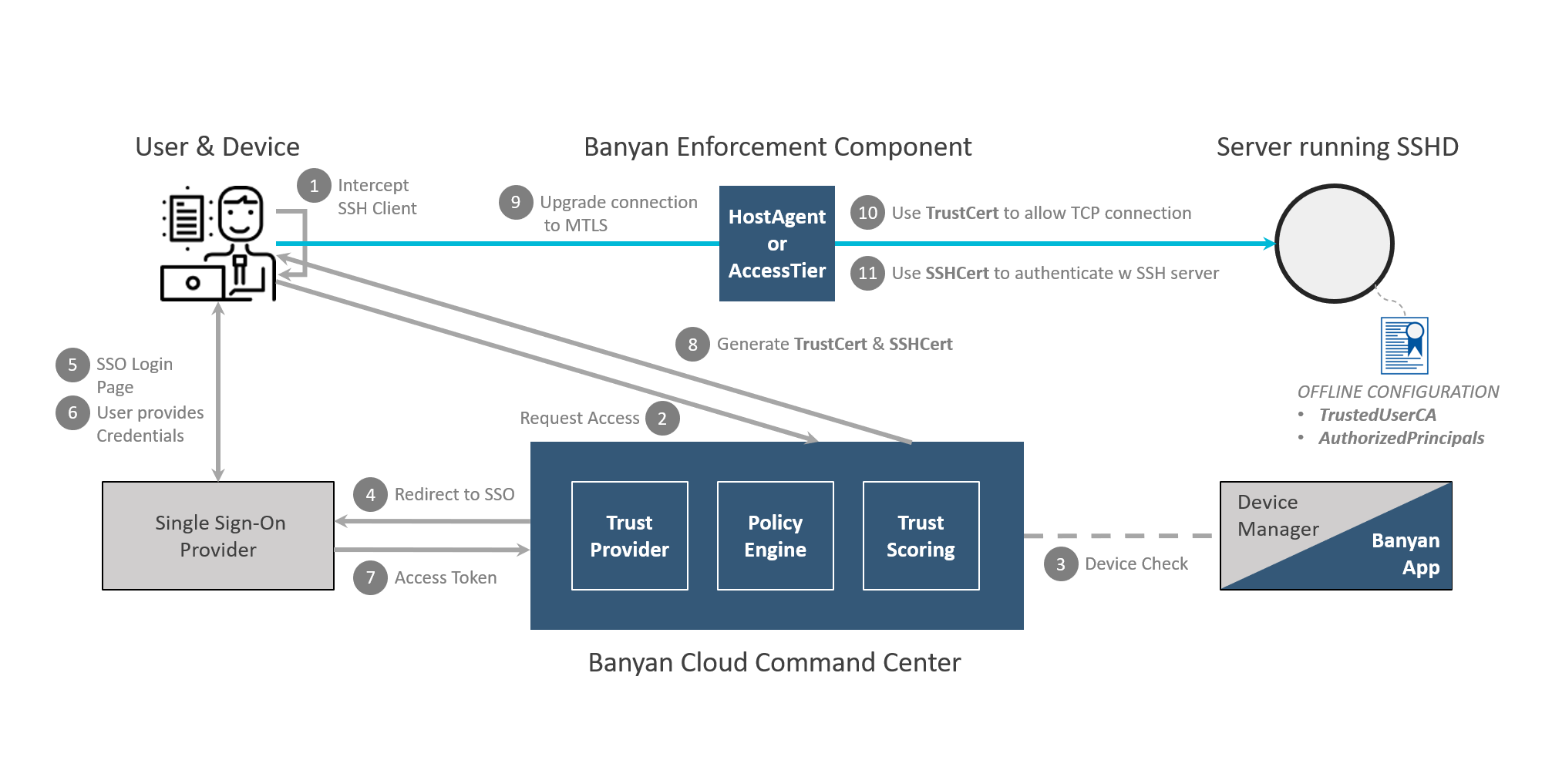
Kollega morbiditet i gang SSH Authentication and Certificate Authority | KEYPER: Manage SSH Key and Certificate Based Authentication